yup... more progress.
I had to create an entry under my saml2auth with
id - https://zulipsp.mysite.com
url - https://zulipsp.mysite.com/saml/metadata.xml
The error is gone and now I have a failed to load key file error:
2021-05-29T15:17:10 ERROR Zope.SiteErrorLog 1622301430.80.20729305271 https://samldemo.alteroo.com/saml2idp/redirect
Traceback (innermost last):
Module ZPublisher.Publish, line 138, in publish
Module ZPublisher.mapply, line 77, in mapply
Module ZPublisher.Publish, line 48, in call_object
Module dm.zope.saml2.browser.role, line 43, in redirect
Module dm.zope.saml2.browser.role, line 78, in _process
- __traceback_info__: <samlp:AuthnRequest
xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol"
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
ID="ONELOGIN_b2d86ca659e7ffecc007c0fcfa370b72af12d6a3"
Version="2.0"
ProviderName="SAML Zulip"
IssueInstant="2021-05-29T15:14:26Z"
Destination="https://mysite.com.com/saml2idp/redirect"
ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
AssertionConsumerServiceURL="https://zulipsp.mysite.com/complete/saml/">
<saml:Issuer>https://samlsp.mysite.com</saml:Issuer>
<samlp:NameIDPolicy
Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified"
AllowCreate="true" />
<samlp:RequestedAuthnContext Comparison="exact">
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef>
</samlp:RequestedAuthnContext>
</samlp:AuthnRequest>
Module dm.zope.saml2.idpsso.idpsso, line 99, in handle_AuthnRequest
Module dm.zope.saml2.idpsso.idpsso, line 138, in _okAuthnRequest
Module dm.zope.saml2.role, line 116, in deliver_success
Module dm.zope.saml2.role, line 154, in deliver
Module dm.zope.saml2.role, line 259, in http_post
Module dm.saml2.binding.httppost, line 28, in encode
Module pyxb.binding.basis, line 539, in toxml
Module pyxb.binding.basis, line 520, in toDOM
Module dm.saml2.signature, line 311, in finalize
Module dm.saml2.signature, line 154, in sign
Module dm.zope.saml2.authority, line 406, in sign
Module dm.zope.saml2.authority, line 312, in _get_signature_context
Module dm.zope.saml2.authority, line 324, in _add_sign_keys
Module dm.xmlsec.binding._xmlsec, line 181, in dm.xmlsec.binding._xmlsec.Key.load
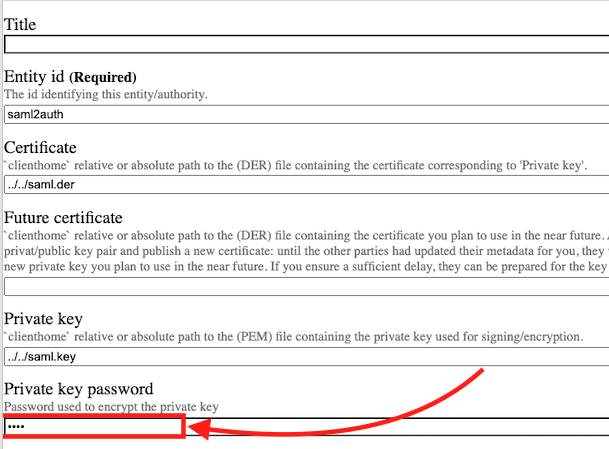
ValueError: ('failed to load key from file', '/home/david/demo.saml2/var/instance/../../saml.key')
I checked and the key file is located at that location. My working guess right now is that the file is incorrectly formatted.
This is how I created the key file and certificates etc..
In the root of my buildout, I generated the key and certificate:
openssl genrsa -des3 -out saml.key 2048
openssl req -new -key saml.key -out saml.csr
openssl x509 -req -days 365 -in saml.csr -signkey saml.key -out saml.crt
Then I created a der file:
openssl x509 -outform der -in saml.crt -out saml.der
I also created a p12 file, which I don't use, but it's there:
openssl pkcs12 -export -out saml.p12 -inkey saml.key -in saml.crt -certfile saml.crt