Preface
Recently, I've been searching for an addon that allows OAuath2 login integrations for Github, Linkedin, Facebook, Twitter and Google Plus. Surprisingly, there's a handy add-on called pas.plugins.authomatic, which is base on the famous authomatic project. Concerningly, the tests are failing. No problem right, it can be patched, fixed or improved, so I tried it out on a dev site. It worked!!!! However, it replaced and disabled the standard login mechanism for Plone, and created custom acl_users.
The Problem
- Users created via the pas.plugins.authomatic aren't Members (membrane users), which defeats the purpose of dexterity.membrane add-on
- Users who didn't use social logins to signup will not be able to log in the standard way since the conventional login method has been disabled.
- plone.login does not work with pas.plugins.authomatic; therefore, custom redirects after login becomes another problem.
Possible Solutions
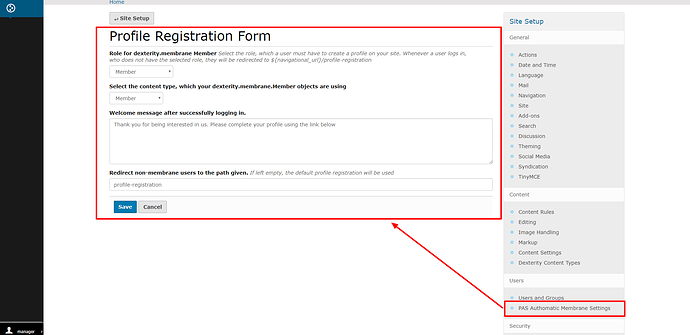
Create a dexterity.membrane.authomatic add-on
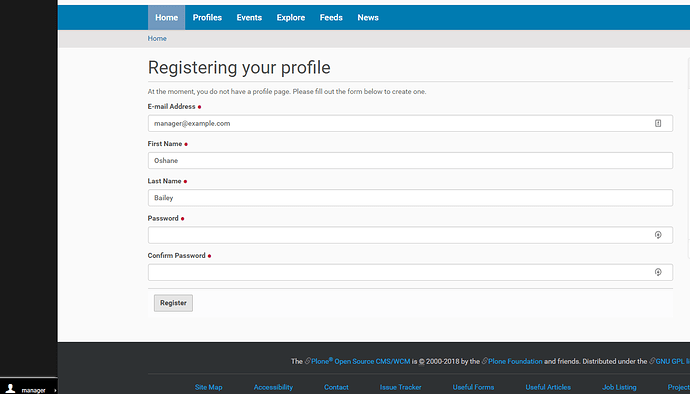
This add-on should turn acl_users to membrane users. Upon on logging in without the given role, the system redirects the user to the profile registration page, where they will complete their profile.
I think this should be optional, meaning, site admin should be able to enable or disable profile registration after login.
I've already started to work on this package. However, I do know how to convert an existing acl_user to membrane user as yet. I think I might have to write a function to copy all the member's property. Any advice?
I've already started to work on this project; it might be useful even outside pas.plugins.authomatic usage. In fact, it might best to merge it with the dexterity.membrane package.
Improving pas.plugins.authomatic
I think its easier to add the following features to pas.plugins.authomatic
- Allow developers to add custom portal pas.plugin tool for handling the result from the various auth providers.
- Allow developers to set the redirect URL after logging in with their auth provider or ensure that plone.login is working with pas.plugins.authomatic
Other important changes:
- Make the redirection from
/loginto/authomatic-handleroptional. If site admins want only social logins, they can do so. Otherwise, keep the standard login method and place the auth providers on the login page. - Use jbot to override the login.pt template and place the auth providers on the login page.
Conclusion
Making these changes will allow a seamless process of logging in with various auth providers and creating a profile if the user wishes or forced to do so based on site settings.
Any thoughts and suggestions?