Running Zope 2.10.6
I've added a PAS plugin. I copied/modified code from the DelegatingMultiPlugin.py file.
My logging shows that much, but not all of it is working.
Here's the code directly from DelegatingMultiPlugin.py
security.declarePrivate('_getUserFolder')
def _getUserFolder(self):
""" Safely retrieve a User Folder to work with """
uf = getattr(aq_base(self), 'acl_users', None)
if uf is None and self.delegate:
uf = self.unrestrictedTraverse(self.delegate)
return uf
security.declarePrivate('authenticateCredentials')
def authenticateCredentials(self, credentials):
""" Fulfill AuthenticationPlugin requirements """
acl = self._getUserFolder()
login = credentials.get('login', '')
password = credentials.get('password', '')
if not acl or not login or not password:
return (None, None)
if login == emergency_user.getUserName() and \
AuthEncoding.pw_validate(emergency_user._getPassword(), password):
return ( login, login )
user = acl.getUser(login)
if user is None:
return (None, None)
elif user and AuthEncoding.pw_validate(user._getPassword(),
password):
return ( user.getId(), login )
return (None, None)
and here's the code from my plugin:
security.declarePrivate('getUsers')
def getUsers(self):
""" Safely retrieve a User Folder to work with """
uf = getattr(aq_base(self), 'acl_users', None)
uf_str = '{aq_base}/acl_users'
if uf is None and self.delegate:
uf = self.unrestrictedTraverse(self.delegate)
uf_str = self.delegate
logger.debug('%s getUsers:uf: %s' % (_get_time(), uf_str))
return uf
security.declarePrivate('mapUser')
def mapUser(self):
"""map the SAML user to a Zope User"""
logger.debug('%s mapUser:enter' % (_get_time()))
acl = self.getUsers()
if not acl:
logger.debug('%s mapUser: no valid acl_users found' % (_get_time()))
return (None, None)
userid = self.token.get('userid')
login = self.token.get('login')
user = acl.getUser(login)
if user is not None:
zu = (user.getId(), login)
logger.debug('%s mapUser:zu: %s' % (_get_time(), zu))
return (user.getId(), login)
else:
user = acl.getUserById(userid)
if user is not None:
zu = (userid, user.getUserName)
logger.debug('%s mapUser:zu: %s' % (_get_time(), zu))
return (userid, user.getUserName)
return (None, None)
First of all, the getUsers function does not find the aq_base acl_users folder. It always returns the delegate folder.
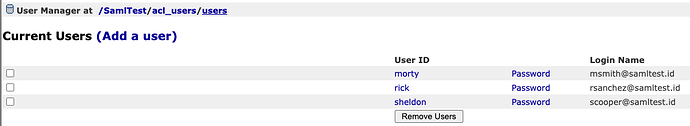
Neither my acl.getUser or acl.getUserById function are returning with a user. My delegate folder absolutely has users matching my SAML users in self.token.
Another issue I am facing, my plugin only runs when I am navigating the ZMI. It does not run when I navigate the actual website.
Any help with Zope 2 PAS plugins will be appreciated.